Opened 14 years ago
Closed 9 years ago
#7660 closed bug (fixed)
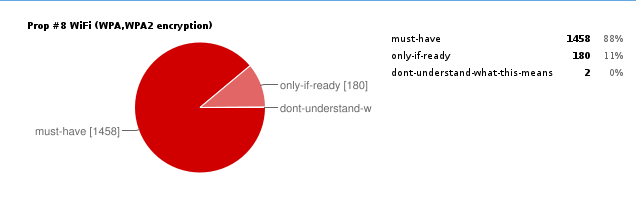
Prop #8 WiFi (WPA,WPA2 encryption)
| Reported by: | scottmc | Owned by: | mmlr |
|---|---|---|---|
| Priority: | normal | Milestone: | R1/beta1 |
| Component: | Network & Internet/Wireless | Version: | R1/Development |
| Keywords: | Cc: | ||
| Blocked By: | Blocking: | ||
| Platform: | All |
Description (last modified by )
Prop #8 WiFi (WPA,WPA2 encryption)
This was voted as a must-have for Haiku R1 and since a requirement for beta1 is to be feature complete, this is a beta1 blocker.
Developer results
- must-have (nielx, pulkomandy, umccullough, czeidler, jprostko, siarzhuk, jonas.kirilla, scottmc, anevilyak, 3dEyes, stippi, axeld, leavengood, mmlr, yourpalal, mmadia, oruizdorantes, colin, zooey, ithamar, korli, laplace, tqh, phoudoin, bonefish, humdinger, Wim, sikosis, brecht)
- only-if-ready none
General poll results
Change History (25)
comment:1 by , 14 years ago
| Description: | modified (diff) |
|---|
follow-up: 3 comment:2 by , 13 years ago
follow-up: 4 comment:3 by , 13 years ago
| Owner: | changed from to |
|---|---|
| Status: | new → in-progress |
Replying to scottmc:
Can we call this one complete yet?
Technically yes, as the encryption and authentication is working with the wpa_supplicant in place. But really I'd see this one a bit broader, as in being usable conveniently in everyday scenarios. For this, storing the credentials and some form of sensible auto-connect still needs to be implemented. I'm taking ownership in any case.
follow-up: 5 comment:4 by , 12 years ago
Replying to mmlr:
Replying to scottmc:
Can we call this one complete yet?
Technically yes, as the encryption and authentication is working with the wpa_supplicant in place. But really I'd see this one a bit broader, as in being usable conveniently in everyday scenarios. For this, storing the credentials and some form of sensible auto-connect still needs to be implemented. I'm taking ownership in any case.
How much is left to do on this? Should we add #7663 as a blocker?
comment:5 by , 12 years ago
Replying to scottmc:
Replying to mmlr:
Replying to scottmc:
Can we call this one complete yet?
Technically yes, as the encryption and authentication is working with the wpa_supplicant in place. But really I'd see this one a bit broader, as in being usable conveniently in everyday scenarios. For this, storing the credentials and some form of sensible auto-connect still needs to be implemented. I'm taking ownership in any case.
How much is left to do on this? Should we add #7663 as a blocker?
I believe so..
comment:6 by , 12 years ago
| Blocked By: | 7663 added |
|---|
comment:7 by , 11 years ago
I think we shouldn't hold this ticket up for #7663, it doesn't make sense.
Is there anything left to implement for WPA/WPA2 specifically?
follow-up: 10 comment:8 by , 11 years ago
| Blocked By: | 7663 removed |
|---|
Yes, there are a few problems left:
- Can't join network with special chars (space or so) in the SSID or key
- Network connection is unreliable and will drop after some time, without any notice.
- wpa_supplicant can be crashed easily, and isn't restarted
- if you enter the wrong key and fail connecting to a network, you have to reboot and start over
comment:9 by , 10 years ago
| Description: | modified (diff) |
|---|
comment:10 by , 10 years ago
Replying to pulkomandy:
Yes, there are a few problems left:
- Can't join network with special chars (space or so) in the SSID or key
Which special characters still can't be used in the SSID? Since alpha 4 I've been able to connect to a SSID with 2 spaces (with a key containing special characters). In recent nightlies, such a key can also be stored with the keystore manager.
comment:11 by , 10 years ago
This may be ok now. I encoutered this issue back then with one of the wifi networks used at BeGeistert, and I can't test it easily here, lacking a secondary wifi AP on which I can test things. If someone has a test access point for this, it would be interesting to test:
- spaces (but as mentionned this may work now)
- special chars (quotes, *, etc)
- unicode (SSID using cyrillic or CJK characters)
Both in the SSID and in the WPA key.
comment:12 by , 10 years ago
#12279 -- Can't join network with special chars (space or so) in the SSID or key
comment:13 by , 10 years ago
| Blocked By: | 12280 added |
|---|
comment:14 by , 10 years ago
#12280 -- Failing to connect to a wifi ap results in the need for a reboot.
comment:15 by , 10 years ago
| Blocked By: | 12279 added |
|---|
comment:16 by , 10 years ago
| Blocked By: | 12281 added |
|---|
follow-up: 19 comment:18 by , 10 years ago
As for "Network connection is unreliable and will drop after some time, without any notice.", is this still an issue? Maybe we just need a simple notification of wifi network connectivity loss?
comment:19 by , 10 years ago
Replying to kallisti5:
As for "Network connection is unreliable and will drop after some time, without any notice.", is this still an issue? Maybe we just need a simple notification of wifi network connectivity loss?
This is generally something the wpa_supplicant is supposed to handle internally. It monitors the network interface and should react to the disassociation event. As long as the configuration isn't changed by attempting to connect to a different network, the settings and credentials the wpa_supplicant uses stay the same. It should therefore attempt to reassociate with the previous access point. I am somewhat certain that I have observed this on my network and that it worked as intended (but it's been quite a while since I actively looked so my memory might play tricks). A reproducible test case would be helpful to confirm/refute this would helpful.
An issue on the lower layers, i.e. FreeBSD compatibility and drivers, could also be at play here. A corresponding log should be gathered by running the wpa_supplicant from the terminal before attempting to connect and then connecting as usual (which should then use the already running wpa_supplicant).
comment:20 by , 9 years ago
| Priority: | blocker → normal |
|---|
No reason to make this blocking a release anymore.
comment:21 by , 9 years ago
I think jua's change to allow disabling wifi N support fixed most of the problems on my machines. Things can still be improved but I think we could consider this ticket fixed and open more specific ones for remaining problems now?
comment:22 by , 9 years ago
| Blocked By: | 12281 removed |
|---|
comment:23 by , 9 years ago
| Blocked By: | 12280 removed |
|---|
comment:24 by , 9 years ago
| Blocked By: | 12279 removed |
|---|
comment:25 by , 9 years ago
| Resolution: | → fixed |
|---|---|
| Status: | in-progress → closed |
Sure, actually already before that; the feature has been implemented. Eventual bugs should be handled in their own tickets.



Can we call this one complete yet?